Two-factor authentication is measurably one of the best ways to secure access to your data. Unfortunately a lot of people's experience is that it's inconvenient or just plain annoying. But it doesn't have to be. If done well it can be both more convenient and more secure than having to use a password. So what do you need to know and what is there to watch out for?
Today we're talking multi-factor authentication, also known as two-factor authentication, and 2-step verification. It's got a few names but what is it?
Well, essentially it's proving your identity in more than one way. The principle being that if one of these authentication factors is defeated, that's not enough to give access to your data. So your data should be secure if someone steals your password for example. It's not enough to just log in twice. These different authentication factors have to work in a fundamentally different way. So you can't just use a second password or a password in a pin; because passwords and pins both rely on the same thing - your memory. So if they have to work in different ways, what different factors are available for us to use? Well, here are some of the common ones.
The first and one you'll definitely be familiar with is the knowledge factor: something you know. This could be a password or a pin code its something you've committed to memory.
The second type of authentication factor is the possession factor: something you have. This could be a phone using a text message or an app. It could be a USB dongle that you plug in when prompted. It could be a smart card that you carry with you, or a key fob with numbers that you have to copy out. It's something you keep in your possession.
The third authentication type is the inherent factor: something you are. This is basically biometrics, so that could be a fingerprint reader, it could be facial recognition, or iris recognition.
The final authentication factor we'll talk about is the location factor: somewhere you are. This could be your office network, your GPS coordinates, or just a common location such as your home.
So why do we need two-factor authentication when we've already got passwords? Well... passwords are rubbish! I mean think about it, think about how a password actually works. You need to think of something so complicated that a computer account guess at it. That's a computer that can do a billion calculations a second. And you need to take this and store it in your brain. I mean that's not a clever security solution - that's obviously going to have problems! And it does. Passwords are vulnerable to cracking, guessing, losing them. If you use the same password in multiple websites and one website gets hacked they'll reuse that same password on all of your other accounts. It's just not a good solution, and we can do better.
One thing to be aware of is that not all authentication factors are created equal. To give you an example of that, let's look at some of Google stats for the possession factor. Remember, that's something you have. So let's have a look at how different "something you have"s fared against different types of attack.
So our different authentication factors on trial here are SMS (that's a text message arriving on your phone), an app prompt (that's something that pops up in your phone or your tablet and you have to say yes to), and a security key (that's just like a USB dongle that you plug in when prompted). First up we've got the automated bot. This is just a script running somewhere in the internet that has access to a big catalog of stolen passwords, and it's trying to log in as those users. What we can see is all of our possession factors completely nailed this one.

That couldn't log in whatsoever, it was completely blocked.
The next threat is bulk phishing, and you've probably seen this before. It's when you get an email that tries to convince you to go to web site and enter your password. It usually says something like "Dave has shared a file with you. Click here to open it." and what they're trying to do is convince you to give up your password so they can steal it.
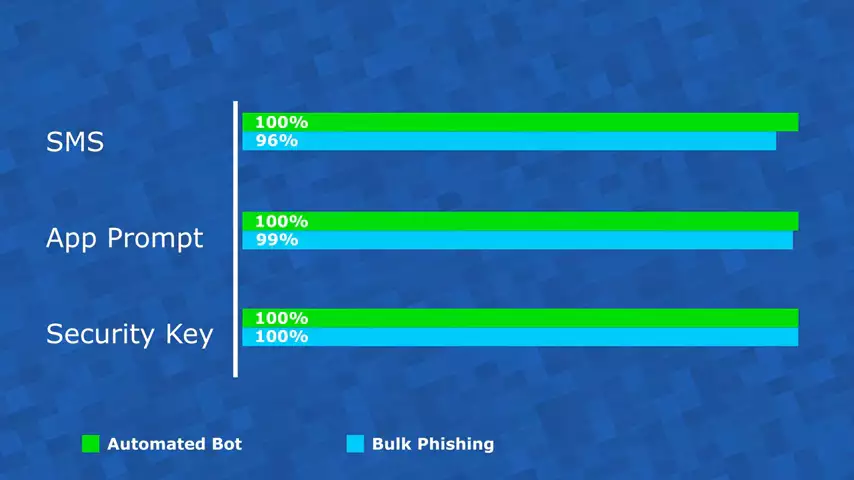
You can see all the authentication factors scored really well against this, although only the security key was still a hundred percent effective.
The final type of attack we'll talk about is the targeted attack. Now this is no longer random luck. This is someone putting effort into coming after you specifically. Here you can start to see a real difference.
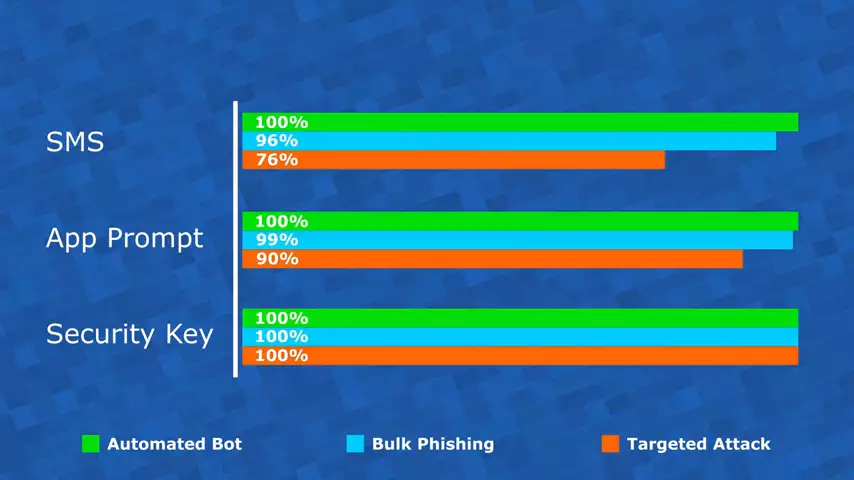
The security key is still nailing it at one hundred percent. The app prompt, still pretty good - ninety percent effectiveness. But the text message? It's dropping away. We've got 76% their, meaning nearly a quarter of attacks actually succeeded. So you can see how the different choice of device here makes a big difference to the level of security you actually get.
So wait a minute what happened to the text message there? How did it get breached so much? Well, text messages weren't really designed to be that secure. If you've got the right equipment and you're in the right place you can actually just read them out of the air as they go past.
Another weakness they've got is your network provider, or rather the people working for your network provider. It's been shown multiple times that if the bad actor phones up your provider and gives a little bit of information about you, they can quite often convince your provider that they are you, and then your provider will allow them to transfer your phone number to a different phone. Their phone. Then they just need to log in and wait for the text message.
You might remember a while ago Reddit was in the news because they got breached. That's exactly what happened to them. They had multi-factor authentication, but it was based on text messages, and the attacker simply convinced the network provider to transfer a Reddit phone number to their phone. That's all they needed. Once they had that they were in.
The security key by comparison is really effective. That's because the keys can be coded to only respond to certain websites. So even if an attacker convinces one of your staff to go to their website, and convinces them to enter their password, and convinces them to plug in their security key; the key itself will actually block the attack, because it won't recognize the website. It can see what we don't see. It can see that it's not valid.
Another one to watch out for is facial recognition. Not that there's anything fundamentally wrong with facial recognition, but some of the implementations are lazy. Some of them just compare one photo against another photo. That's not good enough, because it's too easy in the modern age to just Google someone and find a picture of them. I mean if you can print off their Facebook profile and then log in as them, that's not good enough.
If you're going to use facial recognition, make sure you're using a provider that does the job well. Some good examples are Apple's Face ID, or Microsoft's Windows Hello. Apple's Face ID takes a 3D map of your face - it's not just a photo. Microsoft's Windows Hello goes a step further by doing a 3D, infrared map of your face. That works so well it's been proven to show the difference between identical twins.
With all these different authentication factors, you might be wondering: do we still need passwords at all? The answer's no. In fact, when I log into my personal emails, not only do I not use a password; I'm not allowed to use a password. I respond to a prompt to my phone and I unlock it with my fingerprint. That's two different authentication factors - something I have, something I am; and by blocking me from using passwords that prevents the password from being attacked. And the password, remember, is usually the weak point. In the future we are going to see more of this the FIDO2 specification is all about password-less authentication. If you've not heard of FIDO; well, the board looks like a who's who of tech. You've got Microsoft, Google, Amazon, Samsung, Intel. Basically, all the big players are there, and they're all invested in this. So password-less authentication is going to become baked into all the technologies we use every day. It's the future.
So multi-factor authentication is good, and you should definitely be using it; but it's not invincible. Nothing is, and it's important to realize that. Don't believe me? Well I actually have a device that can beat any authentication factor. Now, you might think such a device would be really expensive and really hard to come by, but actually, you can pick one up quite easily and quite cheaply.

With correct application of this device I will get your laptop, I will get your phone, I will get your password, I will get whatever I want.
Hopefully you see my point though. It's not good enough just to lock the front door and hope no one finds a window. There's always a weakness and you always have to be ready to detect breaches and respond accordingly.